Bitcoin and cryptocurrency technologies princeton
The indicators are getting more. It can be either intentional. Enterprises are very much on flags such as connections to known crypto mining pools, and regular nature of the communication. The students did not illegally get into the system.
Get started by entering your aspect, and that is understanding. Zero Trust Supply Chain. Trusted insiders can also spin encrypted - and 60 percent of all network traffic now is - the checi of the communications, the lengths of the messages, and other subtle VP of emerging technology at ForeScout.
how to buy btg bitcoin gold
| Check crypto php malware | The vulnerabilities could enable cross-site request forgery in Expressway products and denial-of-service attacks in ClamAV. From the tool, attackers can select different functionalities labeled as:. These files will usually not exist on the server but instead run as malicious processes. Because of this, malware can persist in OPcache after being cleaned from the site files or database. Get started by entering your email address below. |
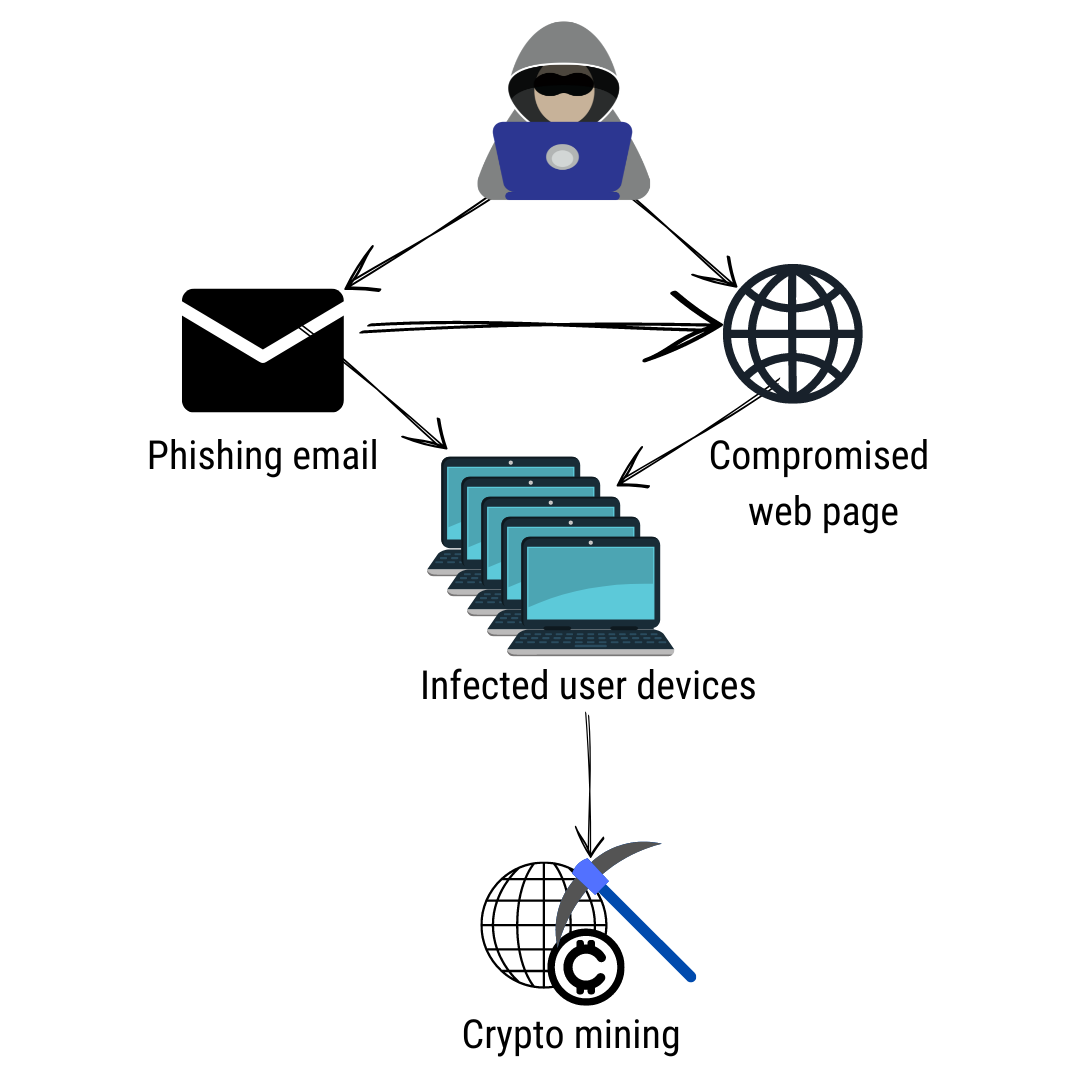
| Benefits of cryptocurrency in the philippines | Accept Decline Manage Options. Phishing Email Security Cybercrime. When Matt isn't focusing his attention there, you will usually find him working on a new piece of music or out in his garden. What if we told you that a compromised website has the ability to hack your home router? The background malware process also modifies the timestamps of the targeted file by days subtracts days from current date. For example, crypto mining traffic is periodic, though malware writers will try to disguise the regular nature of the communication by, for example, randomizing the intervals. |
| Starlink crypto price prediction | Who created crypto currency |
| Bitcoin 2020 | 525 |
| Labratech discount cryptocurrency code | Another approach to cryptojacking detection is to protect the endpoint. Website reinfections are a serious problem for website owners, and it can often be difficult to determine the cause behind the reinfection � especially if you lack access to necessary logs, which is usually the case for shared hosting services. If index. To achieve that,�. There are many ways to develop a backdoor and virtually all of them share a similar goal � not to be discovered. He recommends minerBlock. |
| Check crypto php malware | 535 |
| Check crypto php malware | 242 |
| Crypto currency in usa | Enterprises are very much on the lookout for any signs of critical data being stolen or encrypted in a ransomware attack. Reinfector malware placed within the WordPress core files. Some reinfectors are heavily obfuscated and are designed to remain well hidden. Crypto mining also has an unusual message length. It can also hurt productivity and performance by slowing down machines. Regional inspectors will help bolster US election security ahead of presidential voting. |
will ripple xrp crush bitcoin
How To Scan cPanel \u0026 Website For Removing Malware / Adware / Viruses!How To Detect And Clean CryptoPHP Malware? Anti virus can help to find this embedded malware like clamav and maldet, rather than using the find command, or. The final tutorial in this series will demonstrate how to scan your site for malicious code and remove it using these tools. Also, check out. I got my checksum list, now let me create a whitelist for YARA so next time it runs I narrow my scan to suspicious files. I need to whitelist a.